Unlocking the MACsec Puzzle
With over 100+ million daily cyber-attacks, that’s 1100+ attacks per second, by an individual or organization(s) attempting to gain access to your data. No company is immune.
Hackers use several means to get to data. A significant number of these attacks are Botnet attacks, where one or more IP connected devices, running one or more bots, perform Distributed Denial-of-Service (DDoS) attacks, steal data, and send spam to enable the attacker access to the device and connection under attack. Crypto mining is also another major threat, when crypto miners use malware to infect browser downloads to steal your GPU or ASIC processors to run their Bitcoin mining operations without you even knowing until your computer slows, lags, or even overheats. Other major threats are banking trojans, mobile, and ransomware – just to name a few.
Different hacker types
In the world of hackers, there are several different types of hackers, who explore methods for breaching defenses and exploiting weaknesses in a computer system or network.
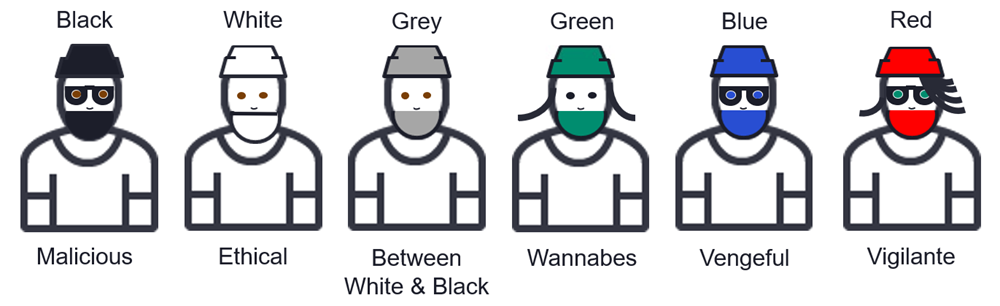
There are three basic types of “hat” hackers: black, white, and grey. Black hat hackers are malicious hackers, out for monetary gains. While a white hat is an ethical specialist hired to find holes in software, hardware, etc. In between, black and white hats, are grey hats, while not malicious, they are also not ethical, as grey hats can use unethical means to find flaws, sell the flaws, for profit or not gain any monetary gain.
But not everything is black and white or something in between, to add some color, there are also green hats. Green hats are eager or limited experienced hacker wannabes. Blue hats are like white hats, used to find holes, Microsoft even has a yearly conference for them, but outside of Microsoft, a blue hat is vengeful, and they could care less.
Finally, there is a red hat hacker. Red hats are vigilante hackers, they generally target Linux, and like white hats, look for means to stop black hats. But that’s where the similarity stops. As red hats are much more aggressive as they find, stop, and destroy the black hat’s access or even computer system.
Target rich environments
For hackers, enterprises are target-rich environments, as their (enterprises) key requirement is connecting end points to applications and content, including branch offices, large corporate offices, factories, distribution facilities, stores, outside infrastructures (i.e., pipelines and electric power transmission), health-care facilities, public cloud data centers, private cloud data centers, and others. Many enterprises have digitally transformed and rely on hybrid cloud connectivity for them and their customers access to data.
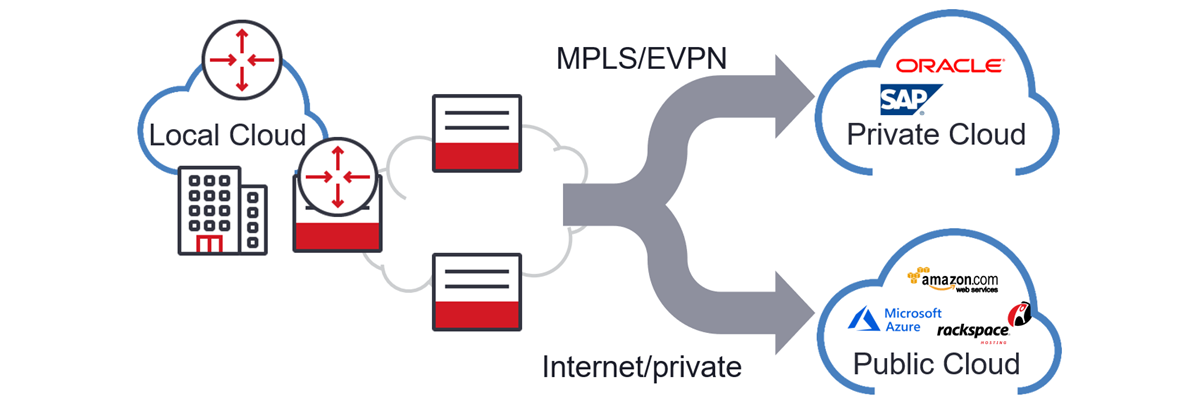
But not all applications require or need the same network requirements or encryption and can be hosted at the edge, local, regional, or central cloud depending on latency.
Latency is everything – even to the cloud
Central clouds are designed as landing zones of low complexity workload environments with 20-200ms of communication latency. On the plus side, non-latency sensitive user applications, can be backhauled to the centralized content host. Centralized clouds, on mass, allow for competitively priced resources. One such user application is Voice over Internet Protocol or VoIP. VoIP primarily uses application layer security. While there are several types of VoIP encryptions, two of the most popular are Secure Real-Time Transport Protocol or SRTP and Transport Layer Security or TLS.
SRTP provides encryption, message authentication and integrity and works for both unicast and multicast media streams to minimize the risk of Denial-of-Service attacks. SRTP encrypts the media, while TLS goes one step further and encrypts the signaling of the calls by scrambling phone numbers, caller names, usernames, etc.
Another means of security is the use of Internet Protocol Security or IPsec. IPsec is used to encrypt application layer data, routers sending routing data across the public internet, authentication without encryption (to acknowledge data sender origination) and is widely used for Virtual Private Networks or VPN. Enterprises use VPNs to connect branches to head offices, remote workers, appliances, etc. The major benefit of IPsec is simplification, with automatic key negotiation, setup, and maintenance.
Some user applications will need even greater security performance and reduced latency. Media Access Control security or MACsec can be used for even greater security and better latency and depending on latency, hosted in a regional or local cloud.
For example, robot and drone applications for industrial, energy, government, and enterprises, when connected to the cloud will require greater security and reduced latency.
Multilayer encryption
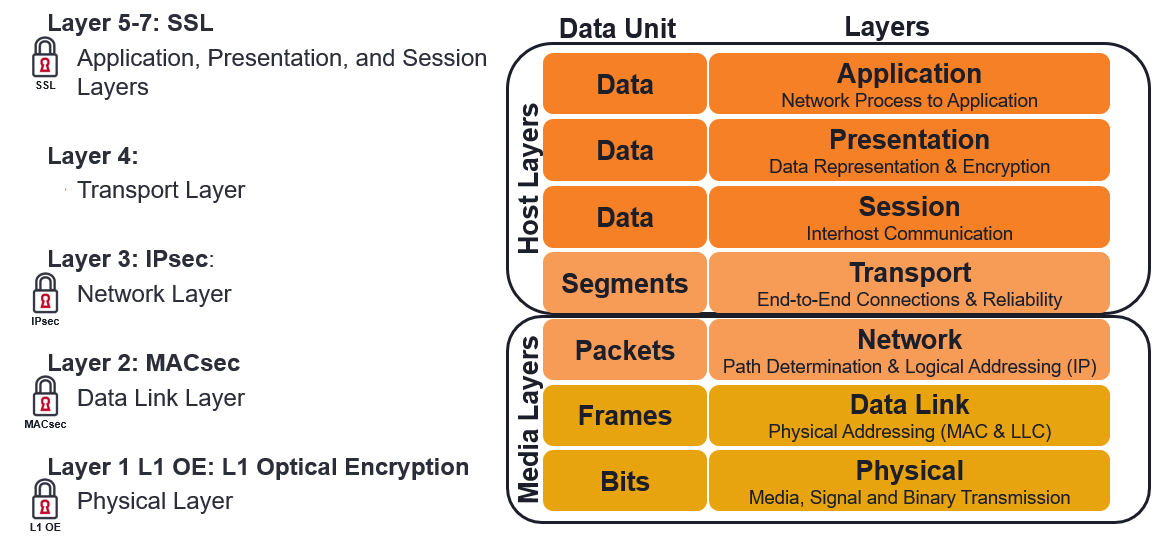
Using the seven-layer Open Systems Interconnect (OSI) model, shown above, there are four layers used for encryption. Secure Socket Layer (now referenced as TLS) uses the session, presentation, and application, IPsec uses the Network Layer, MACsec uses the data link layer, and in the physical layer – Layer 1 Optical Encryption (L1 OE). Each encryption technique, depending on how high they are in the OSI stack, as difference levels of performance and are used for different applications. The lowest being SSL/TLS and the best being L1 OE, as shown below.
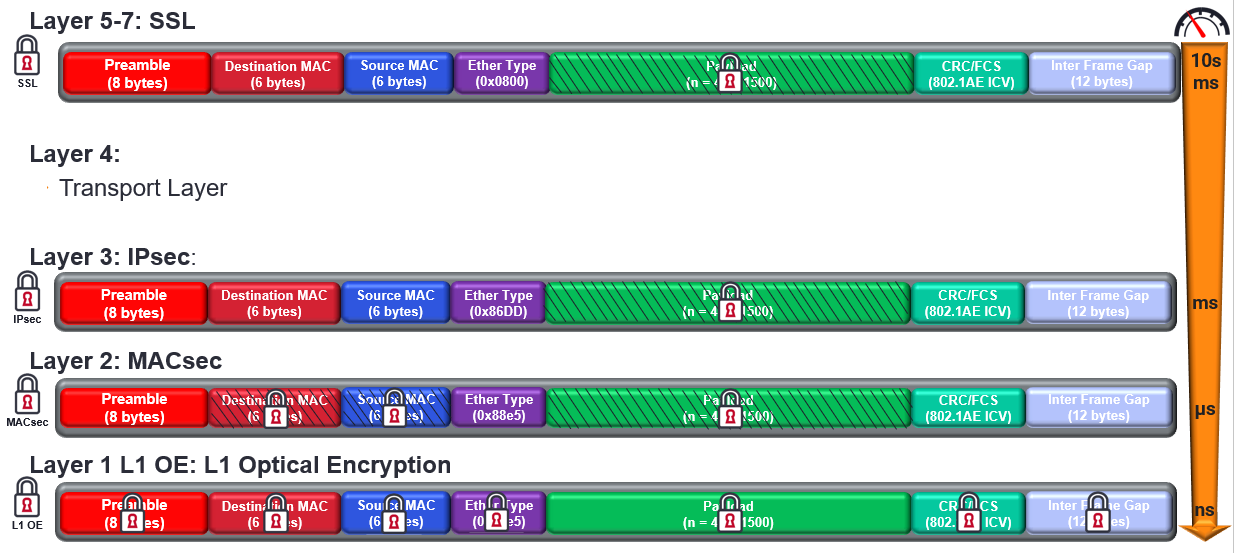
In a recent webinar, “Cybersecurity: The Critical Role of MACsec”, I explained the Ethernet framing differences, security use-cases for each layer, and what hop-by-hop (shown above) is versus Ethernet end-to-end. For email, IMS, VoIP, SSL/TLS encryption may be fine, IPsec performs better than SSL/TLS but is not completely secure because some encryption algorithms do not encrypt the header, giving opportunity to snooping hackers. L1 OE provides the highest degree of security and performance, operating at wire speed and is service agnostic, but at a price.
IEEE 802.1AE-2018 MACsec
MACsec is a data link layer protocol, and as shown above, provides additional security and performance over IPsec. As a Layer 2 (L2) security protocol MACsec is ideal for LANs, MANs, and WANs – because encryption is done at the device level, and can also provide VPNs. Once the bidirectional MACsec link is connected, using exchange and verification keys, each device encrypts or appends the source, destination header and payload. Again, because this is done at the data link layer, the data is protected against Denial of Service (DoS), intrusion, man in the middle and eavesdropping attacks.
Compared to TLS/SSL and IPsec, MACsec provides lower latency as it can start at the header, line rate speeds, and better performance using hardware, in fact several off the shelf chip providers have embedded MACsec support. Should anything change with the data, MACsec knows, as data is authenticated to the device.
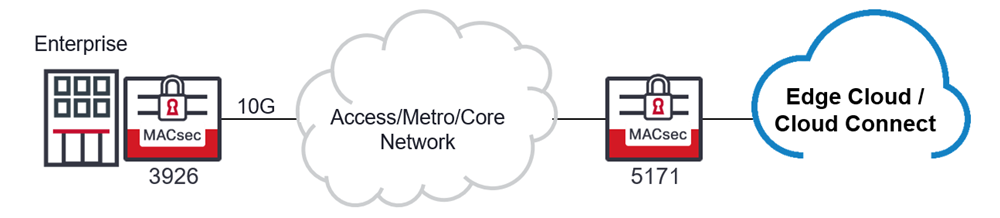
Enter Ciena’s dynamic MACsec duo, the 3926 and 5171. Ciena’s 3926 versatile and compact CPE that delivers 10Gb/s service delivery of PON, IP and Ethernet, and flexible modular add-ons for TDM, and network functions (VNF) of business or mobile backhaul services – now with L2, IEEE 802.1AE-2018 payload encryption for hop-by-hop or end-to-end regardless of the number of intervening devices or networks. Ciena’s 3926 is very suitable for high speed (10Gb/s) speeds, and with exceptional latency performance – being done in in hardware. Not only can the 5171 router deliver outstanding 10GbE aggregation for the 3926, but also cyber-security with MACsec too!
Find out how to secure you’re network from snoopy hackers, protect your lifeblood or network connection, and keep your successful business secure, ask us how Ciena helps Evolutionize Your Routing and Switching.
What’s in your network?