Quantum computing is closer than we think, promising breakthroughs in healthcare, finance, and beyond. However, it also threatens to break the encryption protecting our most sensitive data. Ciena’s Paulina Gomez shares how network operators can start preparing now for the quantum era.
The rise of quantum computing is no longer the stuff of science fiction. It’s rapidly becoming a reality. At its core, it represents a monumental leap in processing power, unlocking immense potential for solving complex problems at speeds classical computers could only dream of. While this holds great promise for revolutionizing industries like healthcare, finance, and logistics, to name a few, it simultaneously exposes critical vulnerabilities in data security.
Traditional cryptographic systems reliant on computational difficulty could become obsolete. For enterprises and network operators handling critical data, the time to prepare for the so-called "Q Day"—when quantum computers become powerful enough to break classical encryption, is now.
Why quantum computing threatens existing encryption
To understand the risk quantum computing poses, it's important to know how modern encryption works. Today, key exchange algorithms are used to generate a shared secret between two communicating parties, which is then used by an AES-256 encryption engine to encrypt/decrypt the data. Current cryptographic systems primarily depend on mathematical complexity. Key exchange algorithms like RSA and Diffie-Hellman are fortified by the difficulty of factoring large numbers or solving discrete logarithms—tasks that classical computers would take millennia to complete. However, a cryptographically relevant quantum computer (CRQC) leveraging algorithms like Shor's, would complete these computations within hours, instantaneously breaking the foundation of classical cryptographic systems. This means that when Q Day arrives, data that is encrypted by these systems will no longer be safe.
Importantly, this risk doesn’t start when quantum computers are fully operational. Threat actors are already anticipating the arrival of CRQCs by engaging in "harvest now, decrypt later" schemes. This involves intercepting and storing encrypted sensitive data today with the intention of decrypting it once capable quantum computers become available. For certain types of critical information that is meant to remain secret—such as personal information, intellectual property, national security data and sensitive financial transactions —the potential impact is significant.
AES-256 encryption remains strong against quantum attacks
While today’s key exchange protocols are particularly vulnerable, the good news is that the AES-256 symmetric encryption algorithm widely used in today’s cryptography is deemed to be resistant against the threat posed by quantum computers. AES-256 relies on a 256-bit key size, and even a powerful quantum computer would take an astronomical amount of time to brute-force all possible key combinations. However, while AES-256 offers a robust degree of quantum resistance, its strength is only as good as the security of the key exchange mechanism used to generate and share encryption keys.
Continuing to safeguard critical data in the quantum era
To combat the threat posed by quantum computing on key exchange protocols, two distinct approaches are leading the charge—Quantum Key Distribution (QKD) and Post-Quantum Cryptography (PQC).
An important benefit of QKD lies in the fact that it is mathematically proven to provide unconditional security of critical in-flight data. Unlike classical key exchange, QKD-based systems are inherently resistant to eavesdropping attacks as they leverage the principles of quantum mechanics to enable secure generation and distribution of cryptographic keys. Here's how it works:
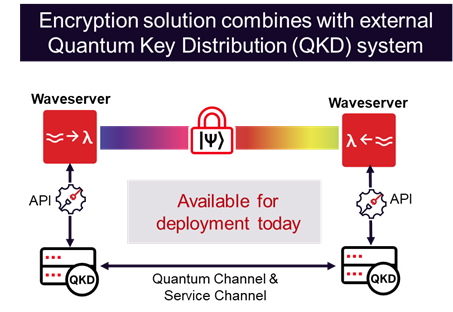 Quantum particles like photons are used to generate quantum secure keys that are locally shared between two endpoints.
Quantum particles like photons are used to generate quantum secure keys that are locally shared between two endpoints.- If the QKD mechanism is intercepted, it will instantly detect the eavesdropping attempt due to the laws of quantum mechanics. This means that if an eavesdropper tries to intercept these quantum particles, the quantum state is modified, making their intrusion readily detectable.
- Using QKD-generated keys with today’s AES-256 encryption systems achieves quantum secure communications.
Several advancements in QKD technology are already making waves. For example, QKD systems can now be integrated with modern optical networks, allowing for seamless collaboration between traditional encryption systems and quantum technology.
PQC presents an alternative by developing new cryptographic algorithms that are considered to be resistant to quantum attacks. Unlike QKD, PQC does not rely on quantum mechanics but uses complex mathematical algorithms believed to remain challenging for quantum computers. The National Institute of Standards and Technology (NIST) took a significant step forward in August 2024, releasing standards for three PQC algorithms to replace vulnerable key exchange protocols. Implementing these algorithms as part of cryptographic systems is conjectured to achieve resistance against quantum computers while offering compatibility with classical networks.
Deploying quantum safe solutions today with Ciena
Although quantum computers capable of breaking today’s encryption methodologies may still be several years away, the time to prepare against this imminent threat is now. This is why Ciena is already helping customers protect sensitive data against “harvest now, decrypt later” schemes by deploying a quantum safe solution using both QKD and PQC over their existing networks. As the leader in high-speed connectivity, Ciena has offered high-capacity optical encryption solutions for over a decade to address the ongoing need to ensure confidentiality of critical in-flight data. In fact, back in 2022, JPMorgan Chase, Toshiba and Ciena were the first to announce the remarkable achievement of quantum securing 800Gbps optical channels at 100 km distance in co-existence mode using Ciena’s Waveserver 5 interconnect platform.
We have come a long way since then with the general availability of this solution that is now deployed in real networks. At OFC 2024, Ciena demonstrated a multi-layered quantum secured strategy to reduce vulnerabilities by combining our 800G optical encryption solution and 400G MACsec encryption solution with two different QKD systems to establish unconditional security of critical inflight data.
Recently, we’ve joined forces with Colt to trial new ways for businesses to overcome the quantum computing threat. And we’ve announced how we are collaborating with REDIMadrid, the research network of Comunidad de Madrid, to lay the foundation required to launch their End-to-End Quantum Secure Data Transport Project. OneFiber Interconnect Germany announced how it is using Ciena’s Waveserver 5 optical encryption solution to support seamless interworking with any QKD system via a standard ETSI API to ensure confidentiality of its customers’ sensitive data across the network.
What’s next?…1.6Tb/s quantum-secure communications!
QKD and PQC are not mutually exclusive. Instead, they can coexist as complementary layers in a hybrid security model, harnessing strengths from both fields.
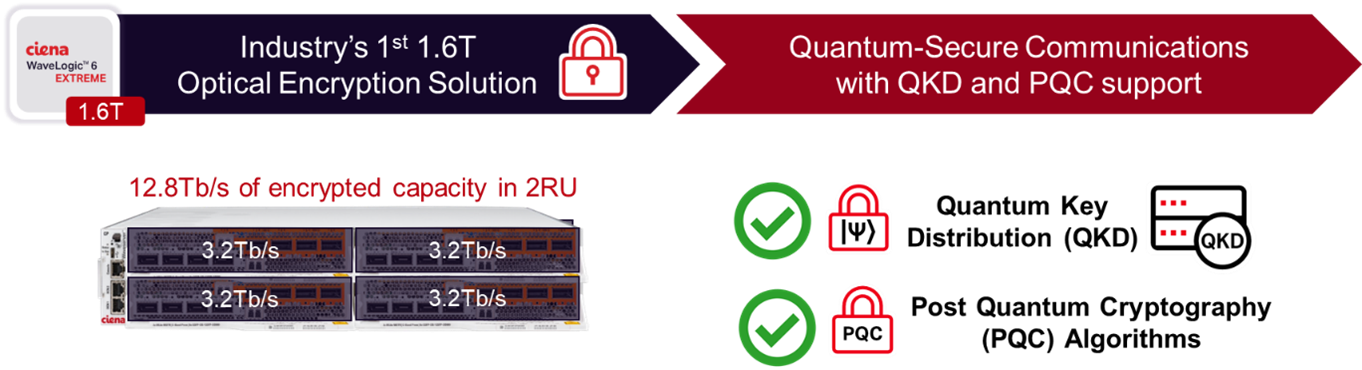
Ciena’s WaveLogic 6 Extreme 1.6T encryption solution was designed with this in mind, supporting seamless interworking with any QKD system vendor as well as NIST-certified PQC algorithms – the choice is yours - to deliver a quantum-resistant solution capable of up to 1.6 Tbps of encrypted capacity per wavelength.
Quantum security is still evolving. Looking ahead, Ciena is engaged in research on advanced technologies for establishing long-distance quantum secured channels. Satellites are emerging as a potential pathway to establish such channels, which is why we have been an active member of the Quantum EncrYption and Science Satellite (QEYSSAT) Project since October 2023 and are recognized as one of the pioneers engaged in this space. We are also conducting research towards establishing long-distance terrestrial quantum communications with futuristic technologies like quantum repeaters, which aim to extend the range of quantum secure channels through entanglement and quantum teleportation methodologies. Stay tuned for more in an upcoming Q&A blog with our Ciena expert Farzam Toudeh-Fallah on this topic.
The time to act is now
The shift toward quantum secure communications is not optional—it is inevitable. Organizations handling sensitive data must act now to mitigate the threat of quantum computing. Ciena's innovative encryption solutions are paving the way to address the challenges ahead – with the industry’s only 1.6T encryption offering, and a solution that supports both QKD and PQC. Contact us to explore how Ciena’s quantum secure solutions help preserve the confidentiality of critical data in an era of advancing quantum technology.







