What Happens When Quantum Physics Meets Cryptography?
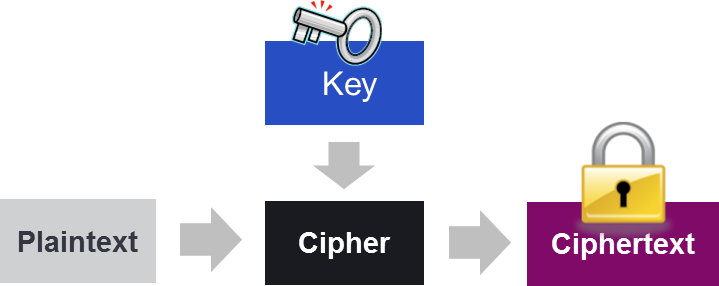
In today’s world of ever-increasing security threats and breaches, encryption is a common technique used to protect critical information from getting into the wrong hands. In cryptography, encryption is the process of encoding a plaintext message in such a way that only authorized parties can access it. The result of this process is encrypted information, also known as ciphertext. But how is this done exactly? The plaintext message is transformed using an algorithm (or cipher) to make it unreadable to anyone except those possessing special knowledge, which is referred to as the key.
As an example, consider encrypted information travelling across a fiber optic cable. A hacker can tap the fiber in an attempt to access the sensitive information it carries, as shown in this video, but encryption prevents a hacker from deciphering the contents of the message without the key.
Luckily, today’s state-of-art secure communications use advanced mathematics to protect in-flight data leveraging highly secure algorithms, such as in Ciena’s WaveLogic Encryption solution. Even though many cryptographic algorithms used today are publicly available, such as the popular Advanced Encryption Standard (AES), they are very difficult to crack in a reasonable amount of time given the computational power of today’s computers. In fact, the keys used in modern cryptography are so large that breaking the AES-256 standard would require “fifty supercomputers that could check a billion billion (1018) AES keys per second [and] would, in theory, require about 3×1051 years.”
The keys used in modern cryptography are so large that breaking the AES-256 standard would require “fifty supercomputers that could check a billion billion (1018) AES keys per second [and] would, in theory, require about 3×1051 years.”
Thankfully this means that there isn't an immediate problem now, but what does the future hold when current computers are replaced with quantum computers? The keys that would take a trillion years to break with conventional computers could possibly be cracked in much less time with quantum computers. And here’s where quantum physics meets cryptography.
The field of Quantum Cryptography is an area of security research and development focused on the introduction of new technologies that will offer more resistance to the computing power of quantum computers. Quantum cryptography draws its strength from the unpredictable nature of photons – the smallest particles in the universe. The foundation of quantum physics is defined by Heisenberg's Uncertainty Principle, which states that observation of these particles in any way changes their behavior. These new quantum cryptography technologies will combine the power of quantum physics and advanced mathematics to deliver maximum security.
Elements of Quantum Cryptography
A key element of quantum cryptography that is being explored to guarantee secure communication is Quantum Key Distribution (QKD). QKD uses photons to produce and distribute a key, not to transmit any message data. This key can then be used with any chosen encryption algorithm (like AES) to encrypt (and decrypt) a message, which can then be transmitted over a standard communication channel.
The main security benefit behind QKD is the ability of the two communicating parties to detect the presence of any third party trying to gain knowledge of the key. This is possible as a direct result of quantum mechanics whereby the process of measuring a quantum system in general disturbs the system changing the particles’ behavior. This means that a hacker trying to eavesdrop on the key must in some way measure it, thus introducing anomalies that can be detected and used to alert the parties that a key has been compromised and should not be used to encode information.
The main security benefit behind QKD is the ability of the two communicating parties to detect the presence of any third party trying to gain knowledge of the key. This is possible as a direct result of quantum mechanics whereby the process of measuring a quantum system in general disturbs the system changing the particles’ behavior.
It turns out that quantum physics can play an important role in delivering maximum security cryptographic systems. According to Born’s rule, the measurement outcome of a quantum state can be intrinsically random, which means that it can never be predicted better than blindly guessing. This key principle of quantum mechanics can be exploited by leveraging the inherent randomness in quantum measurements to generate true random numbers for highly secure cryptographic keys. These types of random number generators are referred to as Quantum Random Number Generators (QRNG) and are not new to the industry. Today, there are several QRNGs that are commercially available that promise true randomness to enable generating cryptographic keys that are impossible to predict.
Last but not least, another area of quantum cryptography that is getting attention is Post-Quantum Cryptography (PQC), also called quantum-resistant or quantum-safe cryptography. Essentially, this is research towards the development of new cryptographic algorithms that would be secure against the computational power of both quantum and classical computers. These next-gen algorithms will serve as replacements for our current public-key cryptosystems to prepare for the day when large-scale quantum computers become a reality. The National Institute of Standards and Technology (NIST) has already started to move in this direction with the kick-off of its Post-Quantum Crypto Project. This project is a process to solicit, evaluate, and standardize one or more quantum-resistant public-key cryptographic algorithms. Nominations for post-quantum candidate algorithms can be submitted up until November 2017. This is same type of process that was put in place by NIST years ago when it was searching for a new algorithm to replace the Data Encryption Standard (DES) published in 1977. This process resulted in the AES-256 encryption algorithm extensively deployed today. These new PQC standards will be used as quantum resistant counterparts to existing standards that are currently available.
The Future of Encryption With Quantum Physics
Today, a hacker can passively intercept an encrypted message sent by Alice to Bob without either of them realizing that their message has been compromised. The hacker can do this in different ways, including fiber tapping, and can then spend lots of time (a trillion years!) and computing power to crack the code.
Now, consider this same example leveraging quantum cryptography. Since we know we can't measure a photon without affecting its behavior, a hacker cannot go undetected when eavesdropping on a private message. After all of the photons are received by Bob, and he and Alice have their conversation about the message transmitted, discrepancies will emerge if a hacker has intercepted the message. If this occurs, the 'transaction' can be aborted, and a new key sent automatically. By sending multiple quantum keys every second, the security of a fiber line can be constantly monitored and attempts to 'tap' the signal can be instantly identified.
As increasingly more sensitive information gets distributed across fiber-optic networks, today’s web-scale communications employ robust optical in-flight encryption solutions to ensure that data is secure, whether it is traveling across the city, across borders, or across the ocean. As the quantum compute era approaches, research and development advances in the area of cryptography are important to ensure that we will be able to continue to secure critical data and the network used to transport it across the globe.